# Notes
# Security
- Authentication 鉴定
- Authorization 授权
- Declarative (annotations, XML)
- Programmatic
# Java EE Security
- Roles 角色
- Realms 领域
- Users
- Groups
- Formerly configured as GF security realm
以前配置为 GF 安全领域 - JSR375:
@DatabaseIdentityStoreDefinition
# web.xml vs JSR375
Declaring Security Roles
声明安全角色<!-- Security roles used by this web application --><security-role><role-name>manager</role-name>
</security-role><security-role><role-name>employee</role-name>
</security-role>@DeclareRoles({”manager", ”,”employee"})Security Constraint
安全约束- Web Resource Collection
网络资源收集<web-resource-collection><url-pattern><http-method> - Authorization Constraint
授权约束<auth-constraint><role-name> - (User Data Constraint)
用户数据约束
- Web Resource Collection
@ServletSecurity(@HttpConstraint(rolesAllowed = ”foo"))
<!-- SECURITY CONSTRAINT #1 --> | |
<security-constraint> | |
<web-resource-collection> | |
<web-resource-name>wholesale</web-resource-name> | |
<url-pattern>/acme/wholesale/*</url-pattern> | |
</web-resource-collection> | |
<auth-constraint> | |
<role-name>PARTNER</role-name> | |
</auth-constraint> | |
<user-data-constraint> | |
<transport-guarantee>CONFIDENTIAL</transport-guarantee> | |
</user-data-constraint> | |
</security-constraint> | |
<!-- SECURITY CONSTRAINT #2 --> | |
<security-constraint> | |
<web-resource-collection> | |
<web-resource-name>retail</web-resource-name> | |
<url-pattern>/acme/retail/*</url-pattern> | |
</web-resource-collection> | |
<auth-constraint> | |
<role-name>CLIENT</role-name> | |
</auth-constraint> | |
<user-data-constraint> | |
<transport-guarantee>CONFIDENTIAL</transport-guarantee> | |
</user-data-constraint> | |
</security-constraint> |
- Authentication Mechanism
认证机制<login-config><auth-method>FORM</auth-method>
<realm-name>file</realm-name>
<form-login-config><form-login-page>/login.html</form-login-page>
<form-error-page>/error.html</form-error-page>
</form-login-config></login-config>@CustomFormAuthenticationMechanismDefinition
# Form-Based Authentication
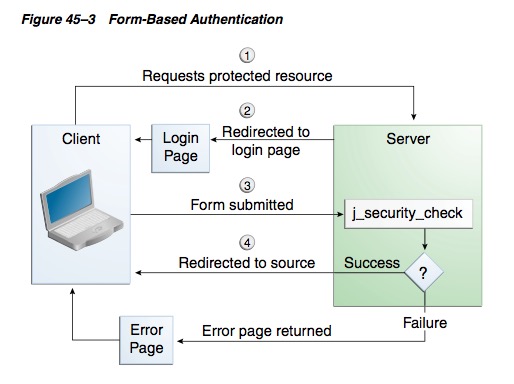
# Role Mapping payara-web.xml
Group to Role Mapping
Layer of Abstraction for Users and Groups
In payara-web.xml , map users and groups to roles:
<security-role-mapping> | |
<role-name>BOSS</role-name> | |
<principal-name>bob</principal-name> | |
</security-role-mapping> | |
<security-role-mapping> | |
<role-name>ADMIN</role-name> | |
<group-name>it-admins</group-name> | |
</security-role-mapping> |
# Final Project
Securing and “webifying” your domain:
- Enhance Model
- Stateless EJBs (Db Operations)
- Singleton EJB (DatabasePopulator) or SQL Load
- Web Application Security
- authN
- authZ
- Presentation and Functionality using authenticated user in JSF
# Important – Java Standards
- Javadoc Analyzer
- Naming Conventions
# Lab
# Summary
The purpose of this assignment is to configure Jakarta EE security in our projects to be used by a JSF login process.
# Requirements
# Documentation
Create a wiki page in your personal space titled Lab 9.
# Database Setup
Use your itmd4515 database and user from Lab 2 - Setup and Introductory Webapp.
# Project Setup
Your uid-fp repository should already be setup, and you should continue pushing your commits into GitHub for this lab. Use a prefix of Lab 9 on your commit messages so I can distinguish them from other labs.
Deviating from the package convention given above will mean that you can not benefit from Sonar and other automated tools, and I will not be able to fix this. Please follow the specification!
# Project Requirements
You should add these changes to your uid-fp project.
Make sure you are following standard Java naming conventions. Please review the following if you are not sure what those naming conventions are:
- Java 8 Pocket Guide by Patricia Liguori, Robert Liguori - Chapter 1. Naming Conventions
- Code Conventions for the Java Programming Language - 9 Naming Conventions (dated, but still correct)
You are welcome to follow the design and patterns I used in my examples, but if you find yourself doing so please make sure you provide a reference in your javadoc comments and/or Confluence page explaining that you based your project on “Instructor Example” or “Example from Web.” Always provide references and citations when you use ideas from other sources. Don't copy and paste my code, however, you need to adapt designs and patterns to your own projects and actually write the code yourself.
As demonstrated in class, Introduce Jakarta EE security to your application that incorporates both authentication and authorization. A complete example of this will be provided in class demonstration. You are welcome to follow my example, which made use of Jakarta EE Security, or to explore and introduce your own approach. If you follow my example, you will need to:
正如在课堂上所演示的,将 Jakarta EE 安全性引入到您的应用程序中,该安全性包含了身份验证和授权。课堂演示中将提供一个完整的示例。欢迎跟随我使用 Jakarta EE Security 的示例,或者探索并介绍您自己的方法。如果按照我的示例,则需要:- Create User and Group JPA entities
创建用户和组 JPA 实体 - Associate them to each other with a ManyToMany relationship
通过 ManyToMany 关系将它们彼此关联 - Associate User to your business domain with a OneToOne relationship
通过 OneToOne 关系将用户与您的业务领域相关联 - Create EJB services for the new security entities
为新的安全实体创建 EJB 服务 - Populate data using your existing Startup Singleton database loader.
使用现有的 Startup Singleton 数据库加载器填充数据。 - Create a new application scoped security configuration class using:
使用以下方法创建一个新的应用程序范围的安全性配置类:@CustomFormAuthenticationMechanismDefinition@DatabaseIdentityStoreDefinition@DeclareRoles
- Define XML
security-constraintelements inweb.xml, containing aweb-resource-collectionandauth-constraintto restrict access to URL paths within your application
在 web.xml 中定义 XML 安全约束元素,其中包含web-resource-collection和auth-constraint以限制对应用程序中 URL 路径的访问 - Map your roles to users and groups using the
security-role-mappingXML element inpayara-web.xml
使用 payara-web.xml 中的 security-role-mapping XML 元素将您的角色映射到用户和组
- Create User and Group JPA entities
Important - you must hash your passwords to work with JSR-375 Security! In class we reviewed how to do this with the default Pbkdf2PasswordHash (PBKDF2WithHmacSHA256).
重要提示 - 必须对密码进行哈希处理才能与 JSR-375 Security 一起使用!课堂上回顾了如何使用默认的 Pbkdf2PasswordHash 执行此操作。Build your login process with JSF using JSR-375 security. As demonstrated in class, this requires the following:
使用 JSR-375 安全性使用 JSF 构建您的登录过程。正如在课堂上演示的那样,这需要满足以下条件:- Introduce a
LoginControllerwith validated username and password fields
介绍一个带有经过验证的用户名和密码字段的LoginController - Inject the
SecurityContextandFacesContext
注入SecurityContext和FacesContext - Implement doLogin and doLogout action methods in the LoginController
在LoginController中实现doLogin和doLogout操作方法 - Implement
login.xhtmlanderror.xhtmlpages in Facelets XHTML, binding the fields fromLoginControlleras appropriate
在 Facelets XHTML 中实现login.xhtml和error.xhtml页面,并根据需要绑定LoginController中的字段 - Handle errors appropriately. Log technical exceptions verbosely. Add appropriate context for the user via JSF messages, and display on the view using the JSF messages component.
适当处理错误。详细记录技术异常。通过 JSF 消息为用户添加适当的上下文,并使用 JSF 消息组件在视图上显示。
- Introduce a
Make use of JSF template(s) for your layout. As demonstrated in class, my example was to use a portalTemplate with role-based navbar. You could also opt to use a separate login page template from Bootstrap, and I encourage you to adopt any of their examples that apply more directly to the purpose of your application. Be creative! (Note - we will cover this in full next week)
在您的布局中使用 JSF 模板。正如在课堂上演示的那样,我的示例是将 PortalTemplate 与基于角色的导航栏一起使用。您还可以选择使用与 Bootstrap 不同的登录页面模板,我鼓励您采用他们的任何示例,这些示例更直接地适用于您的应用程序。要有创造力!Provide logout functionality. I expect to be able to logout from your application, and click a link to login again with a different user.
提供注销功能。我希望能够从您的应用程序注销,然后单击链接以其他用户再次登录。Documentation
- Include screenshots and narrative to prove:
包括屏幕截图和叙述以证明:- Your security realm is configured in
Glassfish
您的安全领域是在 Glassfish 中配置的 - Your authentication is working.
您的身份验证有效。 - You know who the authenticated user is
您知道谁是经过身份验证的用户 - You know what role(s) the authenticated user has
您知道经过身份验证的用户具有哪些角色
- Your security realm is configured in
- Make sure you include your username/password combinations in your Confluence page so I can test your application, as well as any steps necessary to create the security realm.
确保在 Confluence 页面中包括用户名 / 密码组合,以便我可以测试您的应用程序以及创建安全领域所需的任何步骤。 - Discuss your experiences, including any difficulties you had or changes you made
讨论您的经历,包括遇到的任何困难或所做的更改
- Include screenshots and narrative to prove:
Please feel free to use Sonar to analyze your code before submitting. I have created Sonar projects for everyone.
Submit to Blackboard
- Right your uid-fp project and select "Clean"
- Go to your NetBeans Projects directory. Create a zip file of the uid-fp folder and submit it to the Blackboard assignment.